For those who have read my first chapter on my book on the Linux Command Line will know it will also cover the basics on Penetration Testing. The objective of the book is to teachers readers to use the Linux Terminal, program simple projects and learn about the Internet. All three skills are valuable and taken together they form an essential set of skills for those working as computer scientist, engineering and data science. The book I am writing consist of a series of short tutorials I wrote some time ago for myself to make up for what I wasn’t learning in class. Later on I gave these tutorials to my own students to use as primer on a particular topic. For this book I have expanded them slightly but they are still in essence short tutorials. To read the chapter on the Linux command line follow the link.
As for Pen testing. I start off with a simple chapter on reconnaissance that will feature tools such as Maltego, theHarvester, WHOIS and Nslookup. I will also show how to filter Google Search results with commands such as ‘site:’, ‘filetype:’ and ‘inurl:’. Consider this to be the first draft of the chapter. So if you find any errors please let me known in the comment section.
Chapter 1 Reconnaissance
The first step in performing a penetration test is to better get to know your target system. A target company may have a website through which they communicate with customers and perform transactions. Visiting this website can give glimpses of possible entry points but in all likelihood you are not allowed access to sensitive areas, but you may be able to glean much information nonetheless.
Paragraph 1 Using Google
Just like when you visited the target website and used your mark 1 eyeball Google also visits websites to index their content for its search engine. The google crawler will scan everything, even security holes. However, you will have to know how to ask the search engine the relevant information. So far you just type keywords into the google search bar, but it also accepts filter commands.
Using site: you can see indexed pages of only your target and not just about the target. As an example, input the following with www.targetwebsite.com being a random website of you’re choosing.
site:www.targetwebsite.com
We can further limit results by using keywords separated by spaces.
site:www.targetwebsite.com secretfiles
The latter will only return pages of the target website that contain the phrase secretfiles
With intitle: you can search for only those websites with the phrase secretfiles in their title
intitle:secretfiles
With inurl: the search is restricted to finding websites with keywords in the url.
inurl:admin
This example will search the url for the word admin and perhaps reveal configuration files.
With the filter filetype: you can search for specific file types on websites. An example could be
site:www.targetwebsite.com filetype:pdf
Which searches for PDF files at targetwesbite.com. Another common filetype that may contain sensitive information is ppt (powerpoint). Use filetype:ppt to find those.
Paragraph 2 Using WHOIS
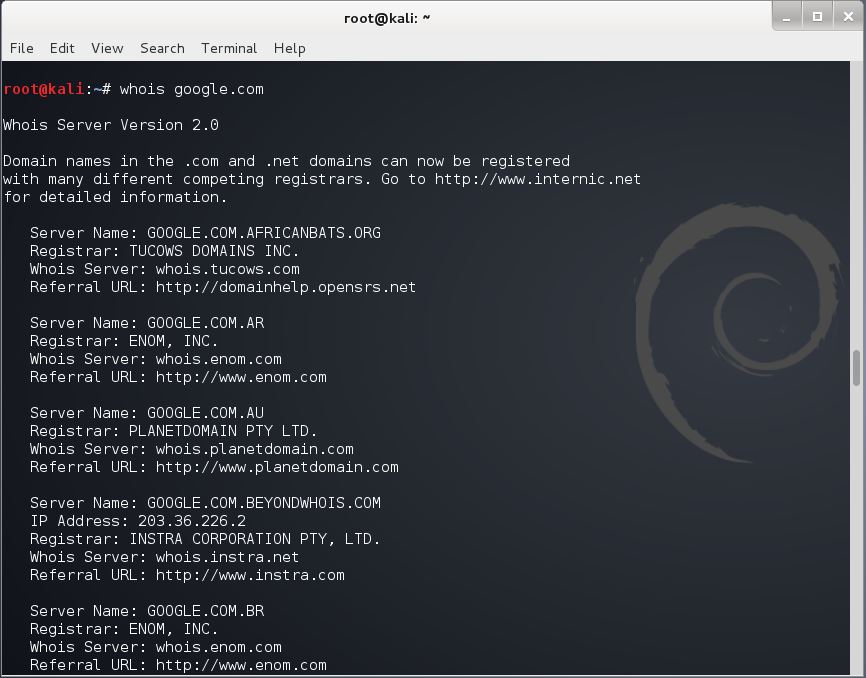
WHOIS is a simple tool built into most versions of Linux. It returns information about a website, not what is on it. There is also a website Whois.net that offers similar functionality. In the command line type in the following string to activate the WHOIS command against your target.
whois targetwebsite.com
An example of output is a follows
Domain Name: TARGETWEBSITE.NET
Registrar: ASCIO TECHNOLOGIES, INC. DANMARK – FILIAL AF ASCIO TECHNOLOGIES, INC. USA
Whois Server: whois.ascio.com
Referral URL: http://www.ascio.com
Name Server: NS01.ONE.COM
Name Server: NS02.ONE.COM
Status: ok
Updated Date: 03-jun-2014
Creation Date: 03-jul-2011
Expiration Date: 03-jul-2015
The first line just returns the official domain name that is registered by the target, but you would already know that. The second returns the registrar that has the website name registered, in this case ASCIO. The two lines containing the words Name Server refer to web servers used by the hosting company to resolve you IP address with a name address. The last three lines are self-evident and describe when the site was created, it status was updated and when it will expire. Going down further in the whois results will reveal personal details about the registrant and the hosting company.
Paragraph 3 Using Nslookup
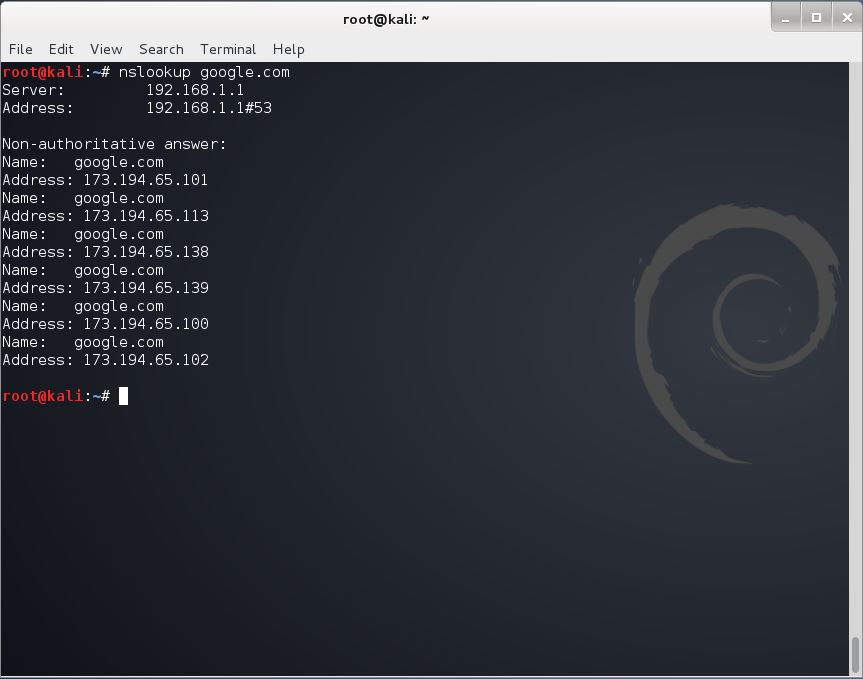
Nslookup (or name server lookup) is handy tool not dissimilar to WHOIS. It allows users, network administrators, to query the Domain Name System (DNS) used to resolve a domain name such as www.targetwebsite.com with an IP address. The tool has a manual that can be viewed with man nslookup.
To query a website just type in nslookup targetwebsite.com
Example output is as follows
Non-authoritative answer:
Name: targetwebsite.net
Address: 123.123.123.1
To use nslookup with just an IP address would get the following result
Nslookup 123.123.123.1
Example output would look as follows
Non-authoritative answer:
39.212.30.46.in-addr.arpa name = webcluster39.one.com.
You may notice the non-authoritative answer, this simply means the name-server queried does not hold the entire zone for the domain.
We can also look at other more exotic records, such as the MX record for email. If a domain such as targetwebsite.com has only one mail server, then the MX record would be mail.targetwebsite.com. With more than one record for a domain the preference number of a MX record is used to indicate where the email should be sent.
nslookup -querytype=mx bbc.co.uk
In the case of the bbc, there are two mx records
bbc.co.uk mail exchanger = 20 cluster1a.eu.messagelabs.com.
bbc.co.uk mail exchanger = 10 cluster1.eu.messagelabs.com.
Paragraph 4 Using theHarvester
TheHarvester is a little tool written in Python by Christian Martorella. With it you can scan the web for email addresses that are related to your target website. Most businesses at least leave some connection to the outside world open such as with FTP, SSH, VPN and webmail to do their business. This leaves them vulnerable to attack from username and password guessing. You would be surprised by the number of people who use the same username for every webservice they use (me included). I strongly suggest you use theHarvester on yourself to discover your own exposure.
To use theHarvester you enter into the terminal the following command
theharvester –d www.targetwebsite.com –l 300 –b all
Here –d is followed by your target domain, -l limits the search with any specific search engine you use and with –b all you signal to use all search engines. The search will include Bing, Google, PGP Key server, Exalead and LinkedIn. Optionally you can include the following behind the command. –f filename which will store results in a file names filename. Adjust the number after –l flag to get more results, but the search will take longer.
Paragraph 5 Using Maltego
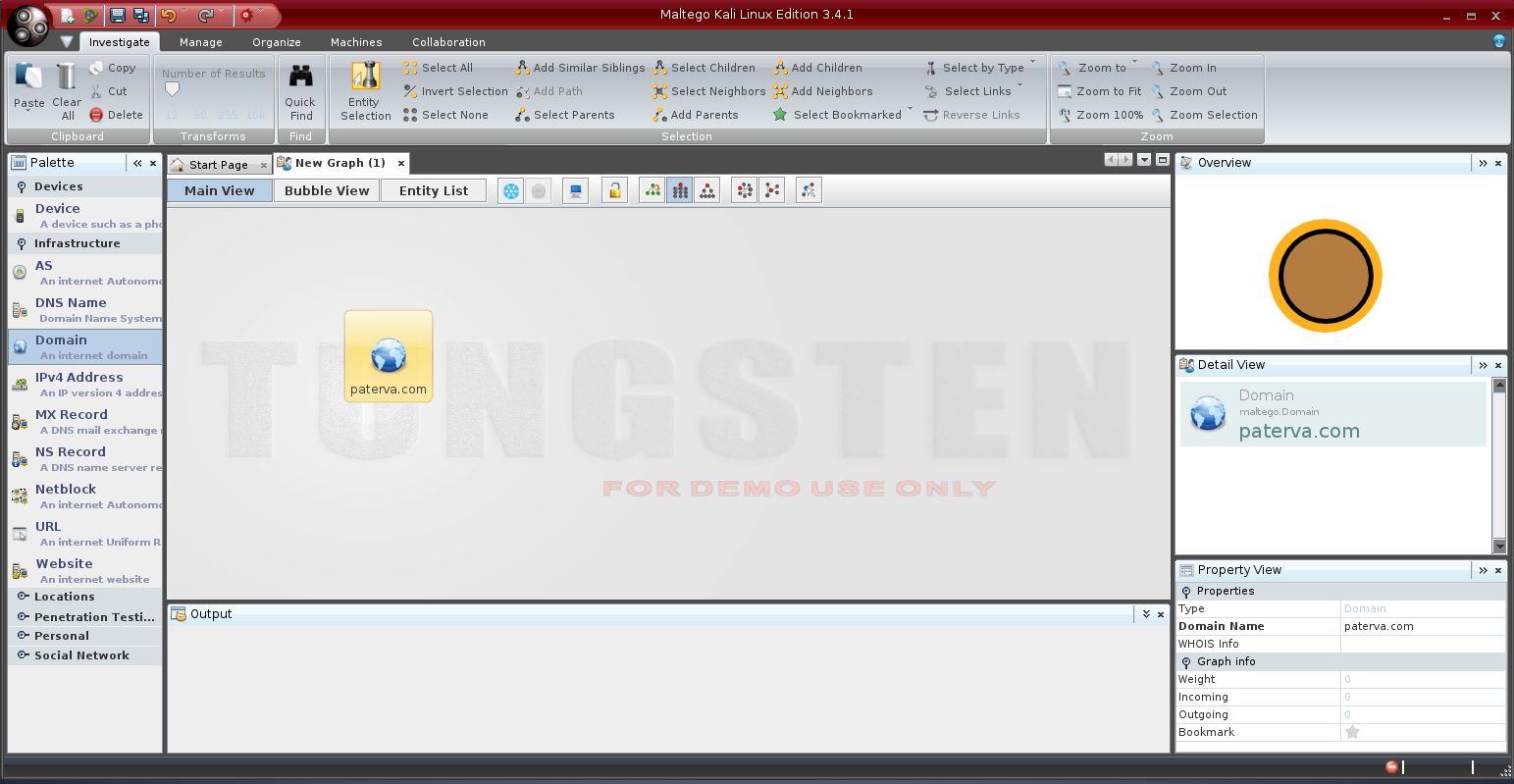
Maltego is an open source intelligence and forensics tool developed by Paterva. It uses data mining on information gathered from open sources and visualizes targets in graphs. For the purpose of this tutorial you will need to create a free account. Type in maltego in the Terminal and complete your account details when prompted. After clicking away more prompts expand you end up with a blank Maltego canvas as seen in the figure below.
In order to use Maltego on a target expand the Palette bar on your left. Drag a Domain on to the canvas in the middle. You will see a Domain entity has been created with paterva.com as its domain. Change this to your target domain by double-clicking the text. To perform ‘transforms’ or queries just right-click on the Domain entity in the canvas and select Run Transforms. You can immediately select Run All Transforms but if you’re target is a large entity this action could take a while. Otherwise select To Website [Quick lookup] or To DNS Name – MX (mail server) to perform a search on the website address or google mail server respectively.
Maltego is a very expensive tool and this tutorial just scratches the surface, but it should give you a mapping of your target domain.
Conclusion
These five tools concludes the reconnaissance part of this book. In practice the number of tool used is countless and all tools described here have many options and flags you can use. Nonetheless, it is counterproductive to get swamped in information on your target. Use these tools initially in an ad hoc way to get an impression of how your target is organized and where they may be weak. Be sure to document all relevant output. Sometimes I print out result and go over them with a red pen to mark possible weaknesses. In the next chapter we will actively scan part of the target system to uncover weak points.
————————————————————————————————
That was it for the draft of the first chapter on penetration testing. Please do use the comment section below if you see any gross errors. This was Reconnaissance with Maltego WHOIS Nslookup
Source; https://www.paterva.com/web6/





Great delivery. Sound arguments. Keep up the amazing effort.